前言
ThinkPHP 5.0.0~5.0.23 RCE 漏洞分析
我用的是5.0.22版本
漏洞分析
exp如下:
1 | http://127.0.0.1/TP5022/public/index.php?s=captcha |
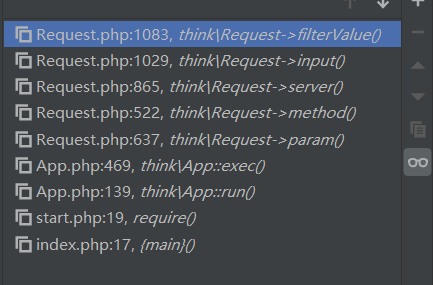
使用debug分析漏洞触发,然后我们跟进这个run()
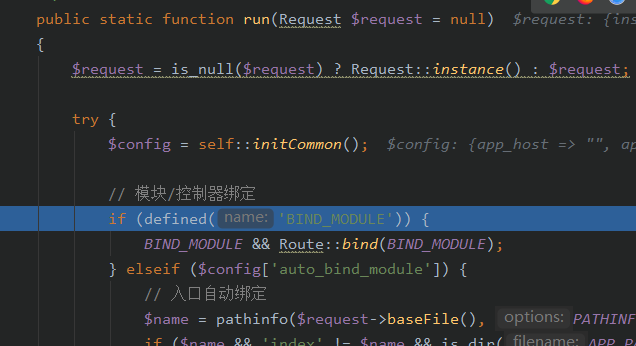
我们的url为http://127.0.0.1/TP5022/public/index.php?s=captcha
在run()中经过一系列的配置加载,后进行url检测
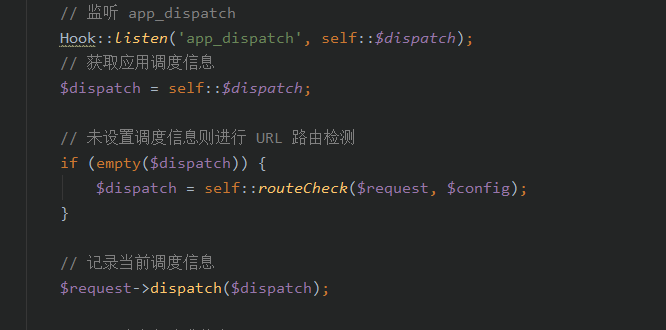
一路跟进至routeCheck()函数
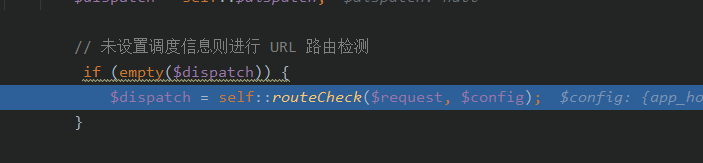
进入这个函数
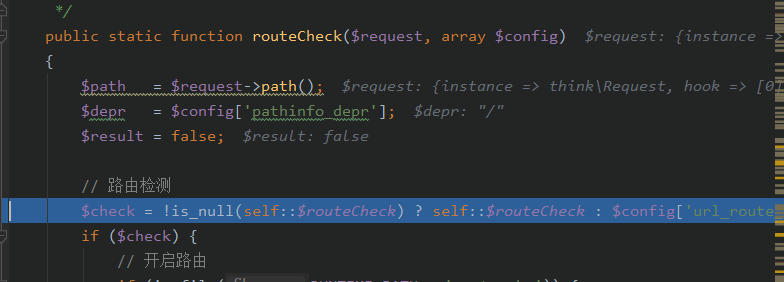
这时候看到debug中获取到
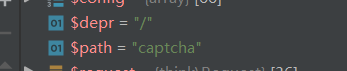
看到路由检测
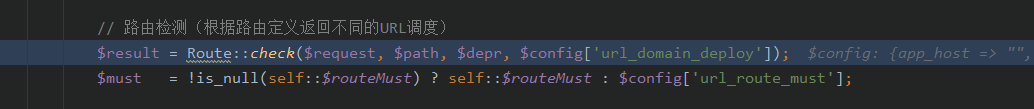
跟进Route::check()函数,在该函数中,我们可以看到
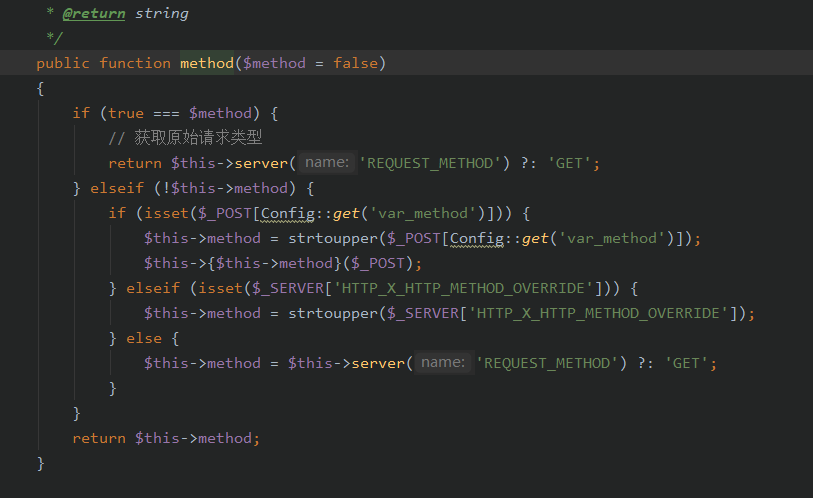
在这个函数中,以下关键代码:
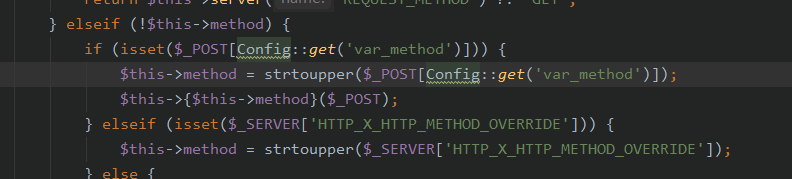
其中var_method为_method,而我们POST了一个_method=__construct
所以这时候
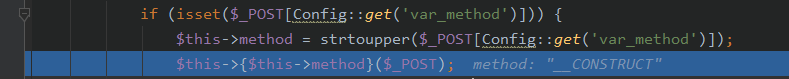
将会去调用,以下函数
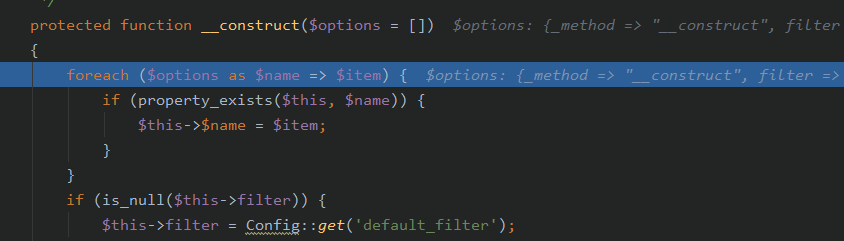
1 | foreach ($options as $name => $item) { |
利用foreach循环,和POST传入数组即可对Request对象的成员属性进行覆盖。其中$this->filter保存着全局过滤规则。经过覆盖,相关变量变为:
1 | $this |
因为我的url如下:
1 | http://127.0.0.1/TP5022/public/index.php?s=captcha |
所以获得
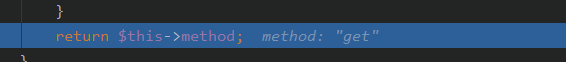
回到run()
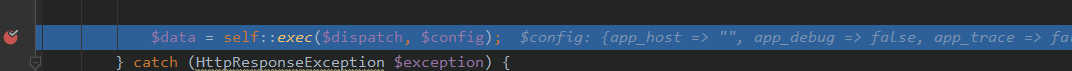
跟进exec(),到case: 'method'
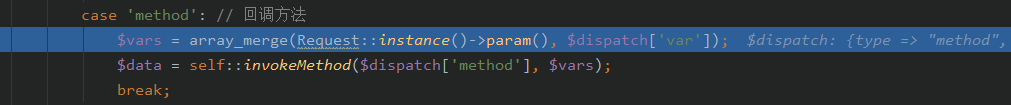
跟进$vars = array_merge(Request::instance()->param(), $dispatch['var']);
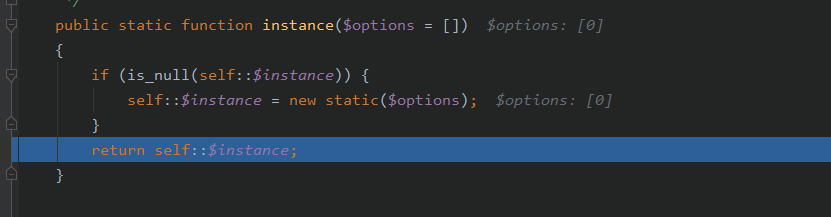
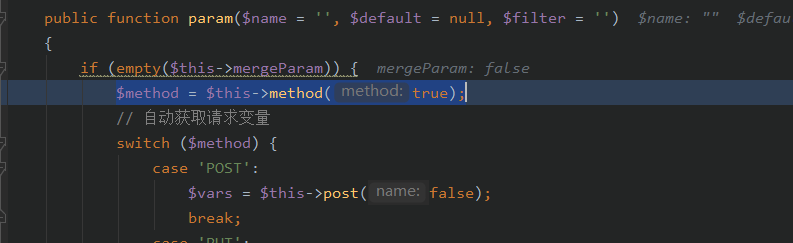
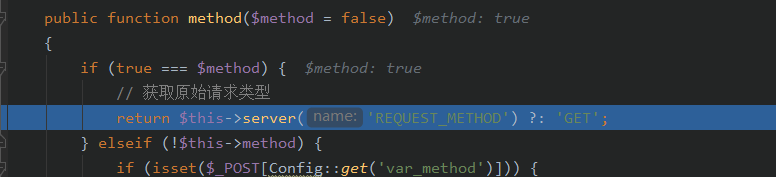
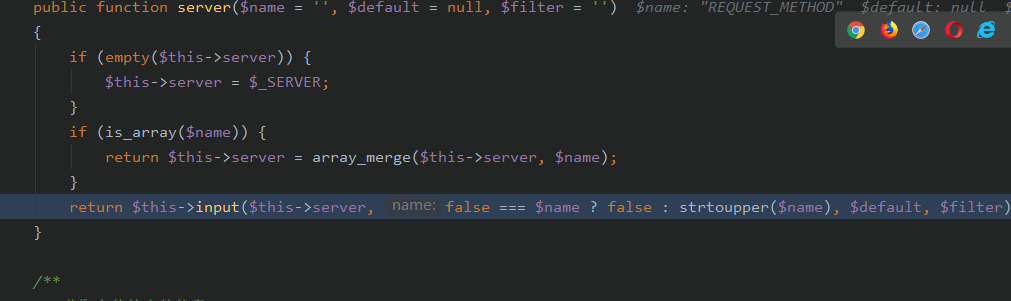
跟进input()
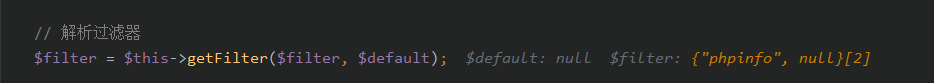
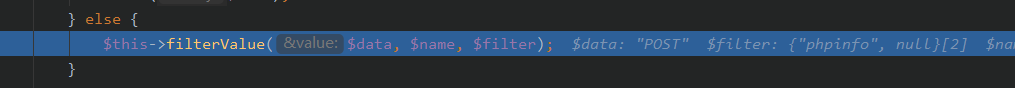
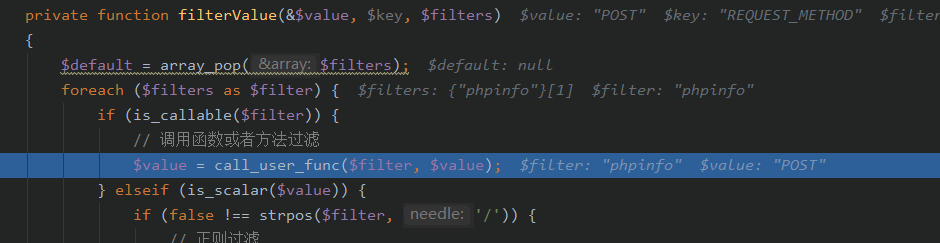
然后调用call_user_func执行phpinfo()
调用栈如下: